In this blog, we are going to see how to implement Single-sign on using Microsoft Azure AD.
AEM ships with a SAML authentication handler. This handler provides support for the SAML 2.0 Authentication Request Protocol (Web-SSO profile) using the HTTP POST binding.
Now let's see what we have to do to configure SAML in AEM.
This includes two major steps first is adding the identity provider(IDP) certificate to AEM truststore. And the second step is to configure SAML authentication handler.
Step 1. adding the identity provider(IDP) certificate to AEM truststore
AEM ships with a SAML authentication handler. This handler provides support for the SAML 2.0 Authentication Request Protocol (Web-SSO profile) using the HTTP POST binding.
Now let's see what we have to do to configure SAML in AEM.
This includes two major steps first is adding the identity provider(IDP) certificate to AEM truststore. And the second step is to configure SAML authentication handler.
Step 1. adding the identity provider(IDP) certificate to AEM truststore
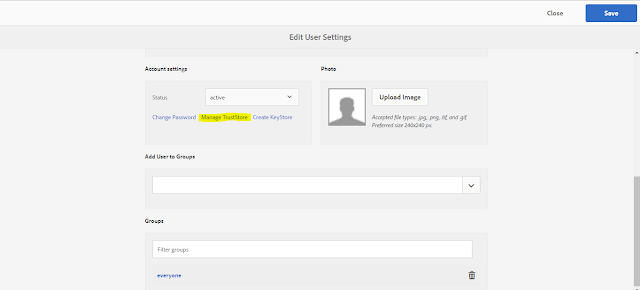
- Go to: http://{server }: {port}/libs/granite/security/content/useradmin.html
- Select any existing user or create new user because TrustStore is global to AEM
- Upload the IdP certificate & make note of the certificate Alias and provide the cert alias in SAML authentication configuration
- Create KeyStore by supplying the password for authentication-service user (default user provided by AEM )
Step 2: configure SAML authentication handler.
- Go to: http://{server }:{port}/system/console/configMgr
- Search for Adobe Granite SAML 2.0 Authentication Handler
- Add the IDP URL
- Add the IDP Certificate Alias which we got in step 1
- Add Service Provider Entity ID()
- Add Password of Key Store(to get this password Select authentication-service and create keystore by giving a password )
- Check Autocreate CRX Users( if it checked it will create a user in crx automatically )
- provide NameIDPolicy Format
- provide Default Groups (A list of default CRX groups in which users are added to after successful authentication)
- Add Synchronized Attributes(list of attribute mappings (in the format "attributename=path/relative/to/user/node") which should be stored in the repository on user-synchronization)
NOTE: Sometimes we have to configure Referrer filter also for SAML
To configure ReferrerFilter go http://{server }:{port}/system/console/configMgr and search for 'Apache Sling Referrer Filter'
provide the hostname which will allow hosts for the referrer.
for reference please visit below links:
for debugging we can use a plugin saml tracer in this we can see what is the SAML response coming
For any query and suggestion please comment or write us an email at rishabhy555@gmail.com





No comments:
Post a Comment